Snyk Fetch The Flag 2025 - TimeOff (Easy)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
TimeOff is an early build for our upcoming line of business application that will help us manage our employee's PTO requests. Please give it a thorough security test and let us know if you find anything. To set you up for success, our devs have given you the full source code and a development build of the current app. Feel free to build a local instance for your security test. If you find anything exploitable, prove it by capturing the flag.txt file on the live instance!
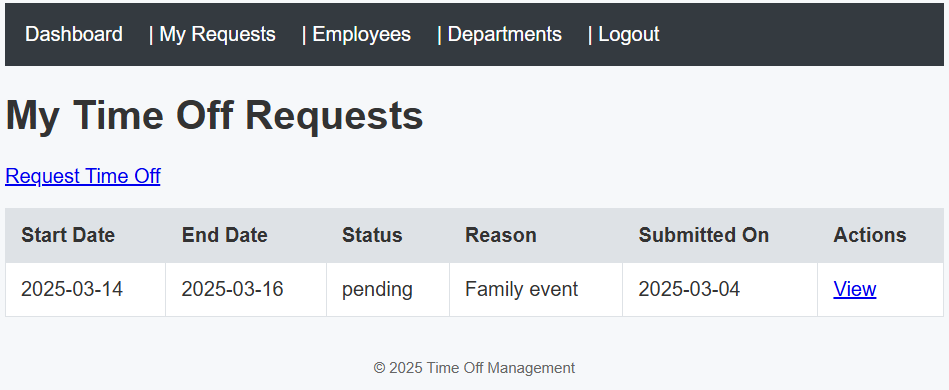
The prompt also gave credentials for a basic user account and an admin account. This is what the basic user sees:
Here is the request form:
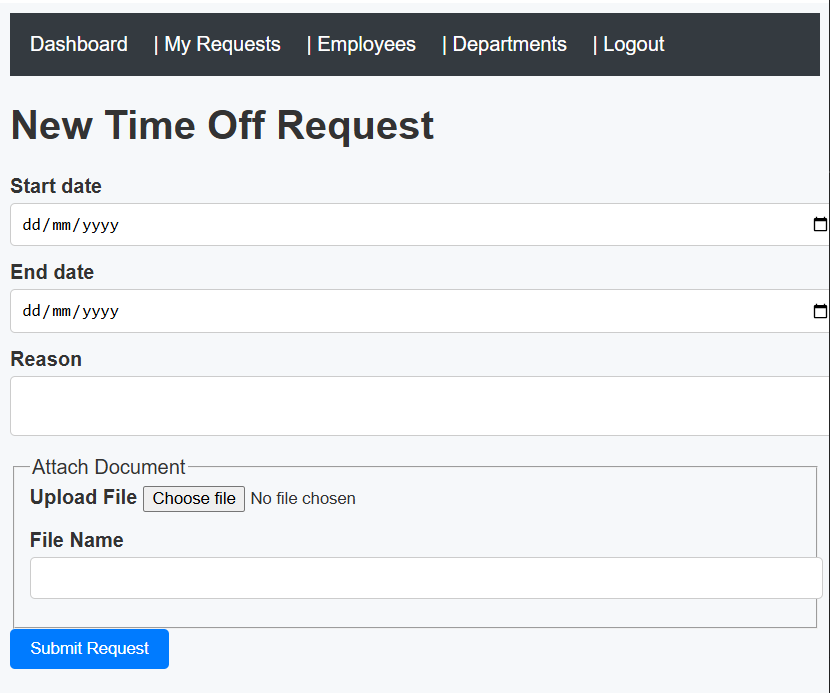
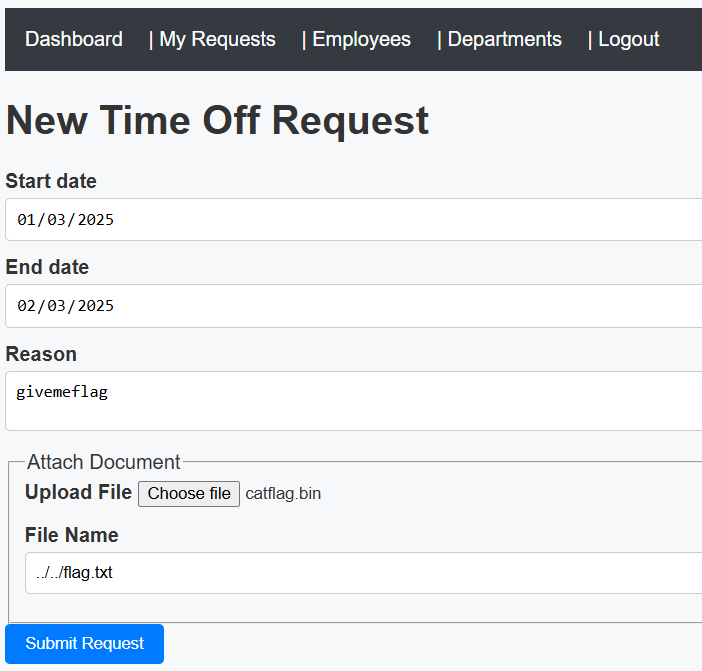
Note that we get to specify the filename indpendently of the name of the file we actually upload. Interesting...
And this is what the admin sees:
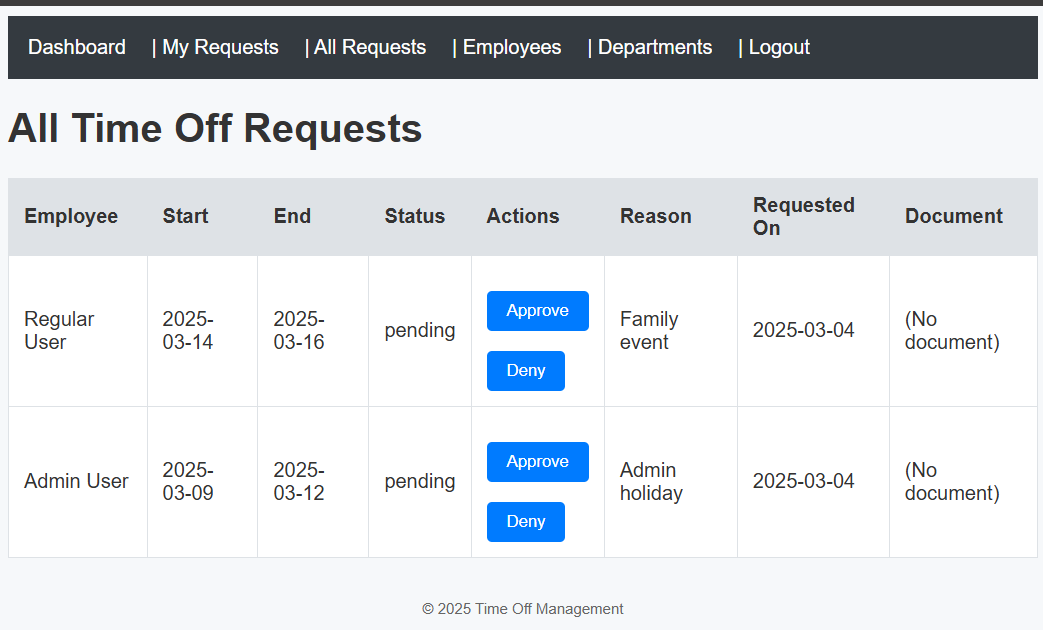
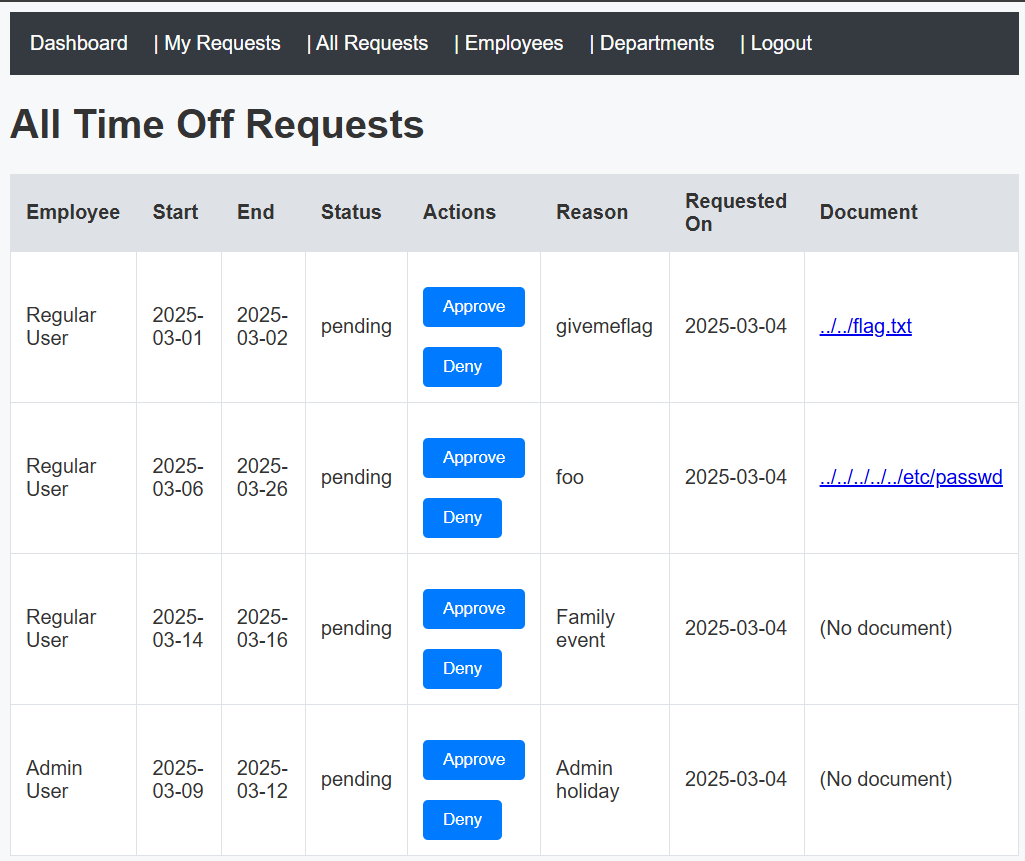
If we submit a request as a user with an attached document, the admin can download it. Looking through the source code, the downloaded file is actually served from the location of the user-supplied file name:

We can also see this clue in the source code, in case we hadn't figured out which parameter had the vulnerability:
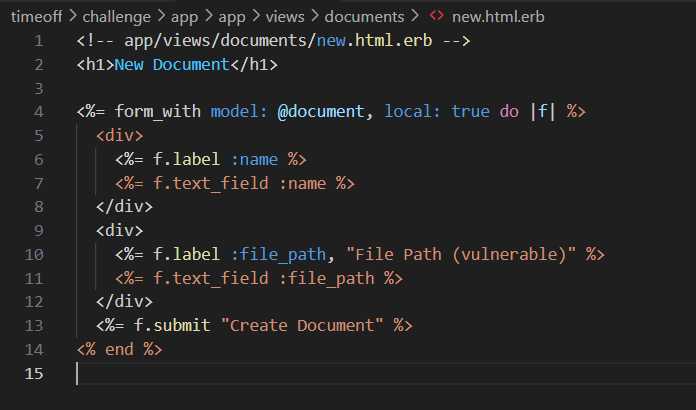
As the user, we submit a request with a filename of ../../flag.txt:
And then as the admin, we can download the flag by clicking the download link in the Document column:
_ Likes