Snyk Fetch The Flag 2025 - Who Is JH (Easy)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
I WANT TO BELIEVE. He can't be all three. Something doesn't add up!
The site looks like this when you load it up:
Looking through the source code for conspiracy.php, we see an absolutely classic local file inclusion:
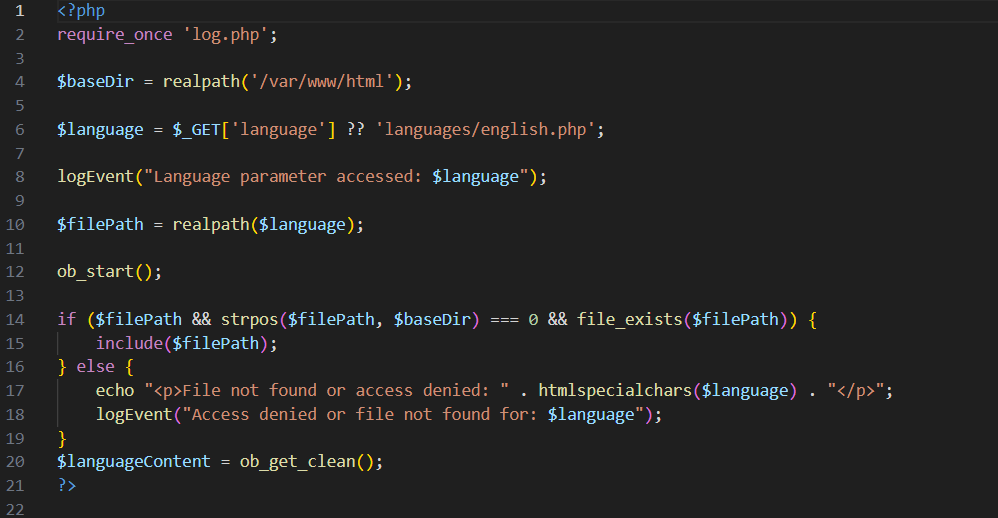
In fact, they have almost fixed it! They check very carefully and correctly that the language file requested is in... /var/www/html. If they didn't check the path at all, we would visit /conspiracy.php?language=../../flag.txt and be done. If they checked that it was in /var/www/html/languages, the vulnerability would disappear. But that wouldn't make for much of a CTF challenge.
We have two paths to victory now:
- Inject PHP code in the log file
- Upload a file with PHP code
Log Poisoning
Let's take a look at log.php:
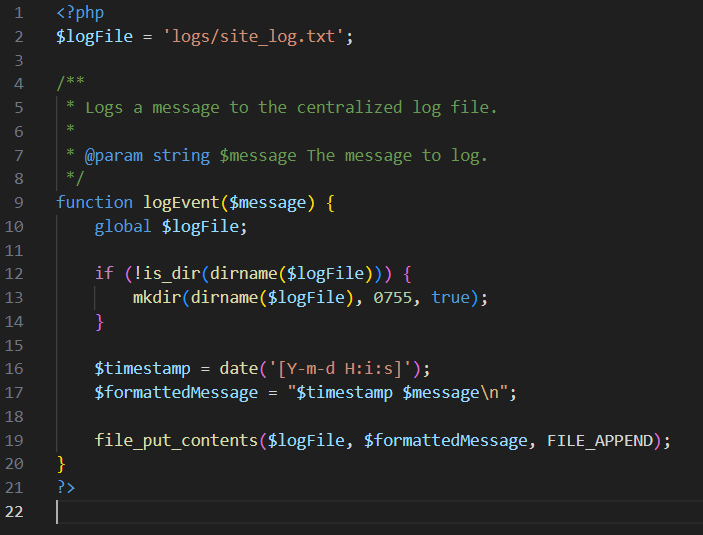
Luckily for us, the message is logged without any sanitisation. And the log file is within the allowed folder, so we'll be able to include it.
We can inject PHP code into the log file by requesting /conspiracy.php?language=urlencode(<?php include("flag.txt"); ?>)
Then we can execute this code by including the log file itself as a "language" if we visit /conspiracy.php?language=../logs/site_log.txt
PHP interprets all text that isn't a <?php ?> tag as just text to be printed.
This gets the flag, and is what I did during the competition, but while I was writing this up, I took another look at the website and realised that it has a file upload page where we can send "conspiracy evidence". Let's have a look at that:
File Upload
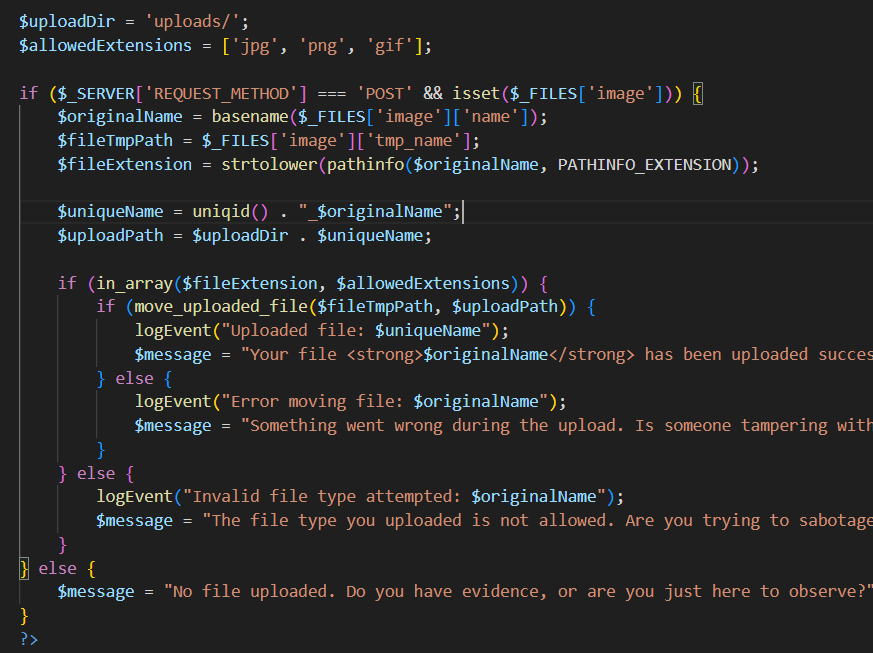
To stop us uploading a file and then including it, the file is saved with a random filename. uniqid is not a secure random number generator. It is derived deterministically from the current time in milliseconds. The server response includes the date and time to second precision, so theoretically we could guess the filename with only 1000 attempts. But we don't even need to.
The name of the file is logged. We can view the logs by including the log file as a language again, or by browsing directly to /logs/site_log.txt. Then we can browse to /uploads/myuniqid.php to execute the payload.
_ Likes